On October 10-11, 2025, a $60 million market dump destroyed $19.3 billion in value. Not through market collapse. Not through cascading margin calls on legitimately impaired positions. Through oracle failure. This wasn’t novel. The same attack pattern has been exploited successfully since February 2020, costing the industry hundreds of millions across dozens of incidents. October 2025 represents a 160x amplification of the largest previous oracle attack—not because of technical sophistication, but because the underlying system scaled up while keeping the same fundamental vulnerabilities. Five years of expensive lessons, ignored. This analysis examines why.
The Oracle Dilemma: Sensitivity vs. Stability
Every leveraged platform faces one fundamental challenge: How do you price collateral accurately while preventing manipulation?
Too sensitive → manipulation attacks Too stable → miss real impairments
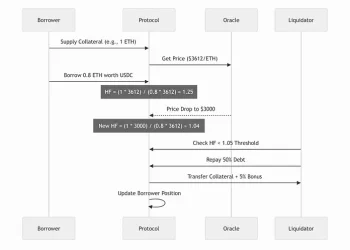
October 2025 chose sensitivity. The oracle faithfully tracked spot prices as $60 million dumped into markets, marking down collateral in real-time, triggering mass liquidations. The system worked exactly as designed.
The design was catastrophically flawed.
The Five-Year Pattern We Refused to See
Before dissecting October 2025, understand this: we’ve been here before.
The Blueprint (2020-2022)
February 2020: bZx ($350K + $630K) Single-source oracle. Flash loan manipulation of Uniswap’s WBTC price. 14.6% of total supply moved to manipulate the feed bZx relied upon exclusively.
October 2020: Harvest Finance ($24M stolen, $570M bank run) Seven minutes. $50M flash loan. Manipulated Curve’s stablecoin prices. Triggered infrastructure collapse and liquidity withdrawal that dwarfed the initial theft.
November 2020: Compound ($89M liquidated) DAI spiked to $1.30 on Coinbase Pro—nowhere else. Compound’s oracle used Coinbase as baseline. Users liquidated based on prices that existed on one exchange for one hour. Required $100K to manipulate orderbook with 300K depth.
October 2022: Mango Markets ($117M) $5M initial capital. Pumped MNGO token 2,394% across multiple venues. Borrowed $117M against inflated collateral. Used stolen governance tokens to vote himself a $47M “bug bounty.” CFTC’s first oracle manipulation enforcement action.
The Common Thread
Every attack followed identical logic:
- Identify oracle dependence on manipulatable source
- Calculate: Cost of manipulation < Extractable value
- Execute
- Profit
From 2020-2022: $403.2 million stolen across 41 oracle manipulation attacks.
Industry response: Fragmented. Slow. Incomplete. Most platforms continued using spot-heavy oracles with insufficient redundancy.
Then came October 2025.
The Anatomy of Oracle Failure: 2025 Edition
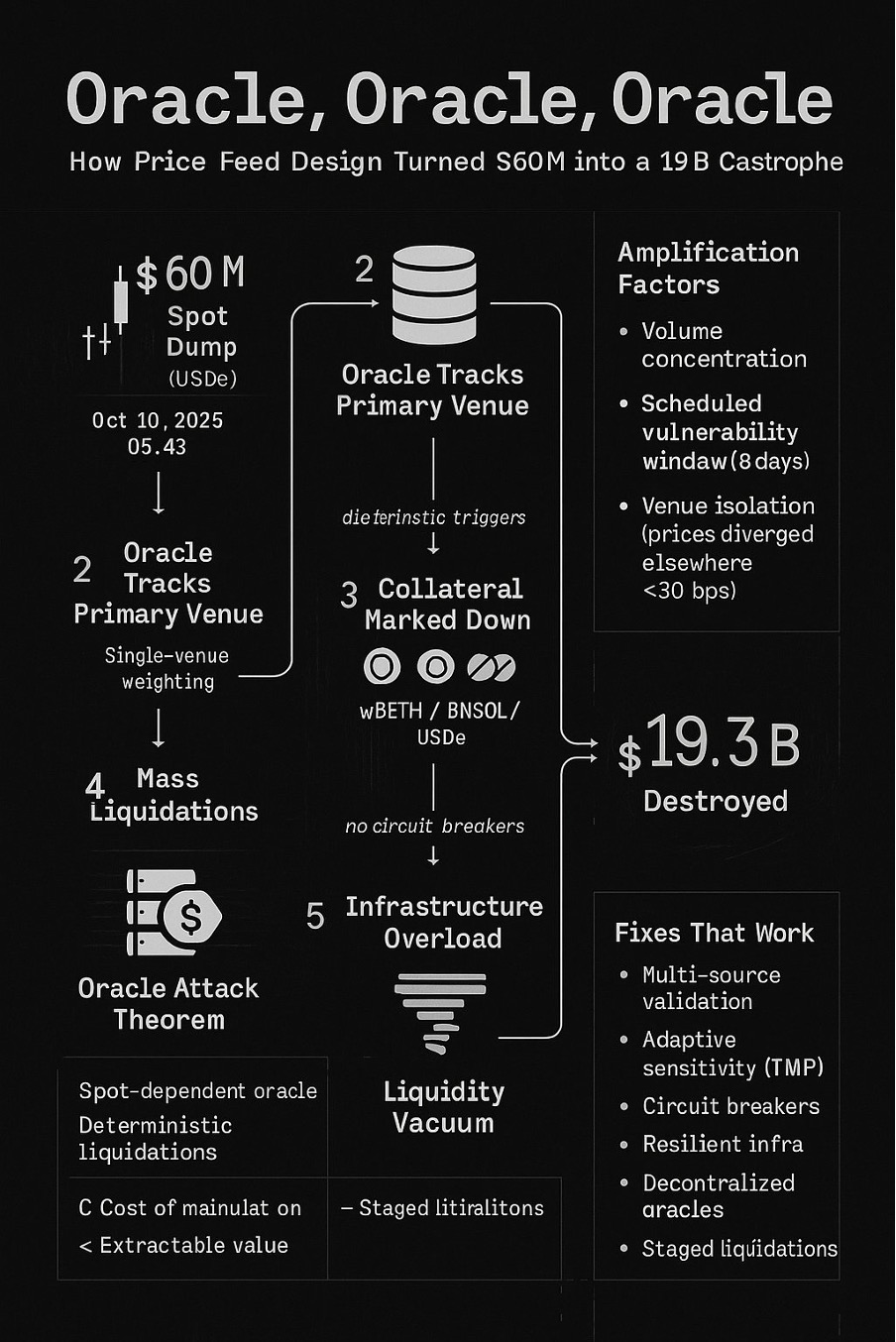
October 10, 2025, 5:43 AM: $60 million USDe dumped into spot markets.
In a properly designed oracle: minimal impact, absorbed by multiple independent sources.
In this oracle: catastrophe.
$60M spot dump → Oracle marks down collateral (wBETH, BNSOL, USDe) → Mass liquidations → Infrastructure overload → Liquidity vacuum → $19.3B destroyed
The Amplification Factor
- Mango Markets (2022): $5M manipulation → $117M extracted (23x)
- October 2025: $60M manipulation → $19.3B destroyed (322x)
Not because of sophistication. Because the same vulnerability existed at institutional scale.
The Weight Distribution Problem
The oracle relied heavily on spot prices from the primary trading venue. When one venue dominates volume:
- High volume suggests price discovery happens there (seems rational)
- But concentration creates manipulation vulnerability (is fatal)
- Using internal prices exclusively creates self-referential loop (compounds the problem)
One analyst’s observation captures the flawed logic: “since [the exchange] has the largest volume of usde/bnsol/wbeth, even based on oracle weights, it should refer to spot price.”
This intuition—trust the biggest market—has destroyed billions across five years of oracle attacks. Volume concentration isn’t evidence of price accuracy. It’s evidence of manipulation opportunity.
The Scheduled Vulnerability Window
Oracle methodology updates were announced eight days before implementation. The attacker had:
- Known oracle dependencies
- Predictable transition timing
- Eight days to position and prepare
Previous oracle attacks exploited existing vulnerabilities. October 2025 exploited the transition between oracle methodologies—a vulnerability that only existed because improvements were announced before implementation.
The Venue Isolation Test
The clearest proof this was oracle failure, not asset impairment:
Primary exchange: USDe at $0.6567, wBETH at $430 Other venues: <30 basis point deviations On-chain pools: Minimal impact
As Guy from Ethena noted: “$9b+ of on-demand stablecoin collateral was available for immediate redemption” throughout the event.
Prices moved dramatically on the oracle’s source exchange while staying stable everywhere else. The oracle reported the manipulated price. The system liquidated based on prices that existed nowhere else in the market.
This is the Compound 2020 pattern: isolated venue manipulation, faithfully reported, systematically destructive.
The Infrastructure Cascade
Analyst agintender identified the amplification mechanism:
“cascade liquidation caused server busy with tons of millions of requests. MMs couldn’t place bids on time that caused liquidity vacuum”
This is the Harvest Finance pattern at scale. The attack triggers liquidations faster than infrastructure can process them. Market makers can’t respond. Liquidity disappears. The cascade becomes self-reinforcing.
After Harvest’s October 2020 infrastructure collapse (TVL dropping from $1B to $599M as users fled), the lesson was obvious: oracle systems must account for infrastructure capacity during stress events.
October 2025 proved we didn’t learn it.
The Sensitivity Trade-off: Two Approaches, One Disaster
Guy from Ethena articulated the core design challenge: Oracles must distinguish between temporary dislocations (market noise) and permanent impairments (real losses).
October 2025 showed two responses:
High-Sensitivity Approach (The Failed Exchange)
- Real-time spot prices
- Fast market response
- Result: $19B cascade
This is the bZx/Harvest approach: trust spot markets, get destroyed by manipulation.
High-Stability Approach (DeFi Survivors)
- Hardcoded USDe = USDT
- Ignore temporary dislocations
- Result: No liquidations
This is overcorrection. Better than failure, but not optimal.
The industry had five years to develop nuanced solutions. We got neither optimal nor acceptable—we got both extremes, with institutional scale choosing the catastrophic one.
The Oracle Attack Theorem: Now Empirically Validated
Theorem: In any leveraged system where:
- Oracle prices depend primarily on manipulatable spot markets
- Liquidation triggers are deterministic
- Infrastructure has capacity limits
Then: Cost of manipulation < Extractable value through cascades
Proof by repeated demonstration:
- bZx (Feb 2020): Uniswap manipulation → $350K + $630K extracted
- Harvest (Oct 2020): Curve manipulation → $24M stolen + $570M bank run
- Compound (Nov 2020): Coinbase manipulation → $89M liquidated
- Mango (Oct 2022): Multi-venue manipulation → $117M extracted
- October 2025: Primary venue manipulation → $19.3B destroyed
As system scale increases linearly, damage scales exponentially. Manipulation cost remains roughly constant (determined by venue liquidity), but extractable value grows with total system leverage.
October 2025 validates the theorem at unprecedented scale.
Oracle Design Principles: Lessons We Should Have Learned
1. Multi-Source Validation
Never rely on single-venue prices, especially from your own orderbooks. This was the bZx lesson from February 2020. Proper oracle design requires:
Oracle Price = Weighted Average of: – Multiple venue prices (40%) – On-chain liquidity pools (30%) – Conversion ratios for wrapped assets (20%) – Time-weighted historical prices (10%)
The weights matter less than the independence. If all your sources can be manipulated simultaneously with reasonable capital, you have one source, not many.
2. Adaptive Sensitivity
Oracles should adjust sensitivity based on market conditions:
- Normal markets: Higher sensitivity to price changes
- Volatile markets: Increased stability through time-weighting
- Extreme moves: Circuit breakers and sanity checks
Time-Weighted Average Price (TWAP) oracles were widely adopted after the 2020 flash loan attacks specifically to prevent single-transaction manipulation. Yet October 2025’s oracles responded to spot prices in real-time, as if the previous five years never happened.
3. Infrastructure Resilience
Oracle systems must maintain functionality during cascade events:
- Separate infrastructure for price feeds
- Capacity for millions of simultaneous queries
- Graceful degradation under load
After Harvest Finance’s infrastructure collapse in October 2020, the importance of system capacity during stress became obvious. Liquidation cascades generate exponentially increasing load. Your infrastructure must handle not just the first liquidation, but the thousandth simultaneous liquidation when market makers can’t keep up and users panic.
4. Transparency Without Vulnerability
The eight-day window between announcement and implementation created a known attack vector. Better approaches:
- Implement changes immediately after announcement
- Use rolling updates without fixed dates
- Maintain audit trails without preview periods
This is a new lesson, though it follows logically from game theory: never announce exploitable changes in advance. The attacker in October 2025 had eight days to plan, position, and prepare. They knew exactly when the vulnerability window would open.
The Academic Perspective: Oracle Attack Theorem
From a theoretical standpoint, five years of empirical evidence proves:
Theorem: In any leveraged system where:
- Oracle prices depend primarily on manipulatable spot markets
- Liquidation triggers are deterministic
- Infrastructure has capacity limits
Then: Cost of manipulation < Extractable value through cascades
Proof by repeated empirical validation:
- bZx (Feb 2020): $10M borrowed, $350K extracted. Oracle manipulation via Uniswap.
- Harvest (Oct 2020): $50M flash loan, $24M stolen + $570M bank run triggered.
- Compound (Nov 2020): $100K orderbook manipulation, $89M liquidated.
- Mango (Oct 2022): $5M initial capital, $117M extracted.
- October 2025: $60M spot dump, $19.3B destroyed.
The progression is clear: as system scale increases linearly, damage scales exponentially. The cost of manipulation remains relatively constant (determined by liquidity in manipulatable venues), but extractable value grows with total system leverage.
October 2025 provides empirical validation at unprecedented scale. The theorem holds.
Systemic Implications: The Lessons Still Not Learned
This wasn’t just one platform’s failure—it exposes industry-wide vulnerabilities that have persisted despite five years of expensive education:
1. Over-reliance on Spot Prices
Most platforms still use spot-heavy oracle designs despite every major attack since 2020 exploiting exactly this vulnerability. The industry knows spot prices are manipulatable. The industry knows TWAP and multi-source oracles provide better protection. Yet implementation remains incomplete.
Why? Speed and sensitivity are features until they’re bugs. Real-time price updates feel more accurate—right until someone manipulates them.
2. Concentration Risk
Dominant venues create single points of failure. This was true when bZx relied on Uniswap, when Compound relied on Coinbase, and when the October 2025 platform relied on its own orderbook. The venue changes; the vulnerability doesn’t.
When one exchange has the plurality of trading volume, using it as your primary oracle source seems rational. But concentration risk in price feeds is like concentration risk in any system: it’s fine until someone exploits it.
3. Infrastructure Assumptions
Systems designed for normal markets fail catastrophically under stress. Harvest Finance proved this in 2020. October 2025 proved we still design for normal conditions and hope stress never happens.
Hope is not a strategy.
4. The Transparency Paradox
Announcing improvements creates attack windows. The eight-day gap between announcement and implementation of oracle changes gave sophisticated actors a roadmap and timeline. They knew exactly when to strike and what to exploit.
This is a new failure mode for an old problem. Previous oracle attacks exploited existing vulnerabilities. October 2025 exploited the transition between oracle methodologies—a vulnerability that only existed because improvements were announced before implementation.
The Path Forward: Actually Learning This Time
Immediate Improvements
1. Hybrid Oracle DesignCombine multiple price sources with sanity checks that actually work:
- CEX prices (with volume weighting across venues)
- DEX prices (from high-liquidity pools only)
- On-chain proof of reserves
- Cross-exchange deviation limits
Each source should be independent. If manipulating one source affects another, you don’t have redundancy.
2. Dynamic WeightingAdjust oracle sensitivity based on market conditions:
- Normal volatility: Standard weights
- High volatility: Increase TWAP window, reduce spot influence
- Extreme moves: Pause liquidations, investigate before proceeding
The Compound attack showed that sometimes the “correct” price on one exchange is wrong for the entire market. Your oracle should be smart enough to know this.
3. Circuit BreakersPause liquidations during extreme price moves—not to prevent legitimate deleveraging, but to distinguish manipulation from market reality:
- If prices converge across venues within minutes: likely real
- If prices remain isolated to one venue: likely manipulation
- If infrastructure is overloaded: pause until capacity restored
The goal isn’t to prevent all liquidations. It’s to prevent cascading liquidations triggered by manipulated prices.
4. Infrastructure ScalingDesign for 100x normal capacity because that’s what cascades generate:
- Separate infrastructure for price feeds
- Independent liquidation engines
- Rate limiting for individual addresses
- Graceful degradation protocols
If your system can’t handle the load during a cascade, it will amplify the cascade. This is a design requirement, not an optimization.
Long-term Solutions
1. Decentralized Oracle NetworksMove to mature oracle solutions like Chainlink, Pyth, or UMA that aggregate across sources and have built-in manipulation resistance. These aren’t perfect, but they’re better than spot-dependent oracles that get exploited every 18 months.
bZx integrated Chainlink after their 2020 attacks. They stopped getting attacked via oracle manipulation. This isn’t coincidence.
2. Proof of Reserves IntegrationFor wrapped assets and stablecoins, validate collateral value on-chain. USDe should be priced based on verifiable reserves, not orderbook dynamics. The technology exists; implementation lags.
3. Gradual LiquidationsPrevent cascade amplification through staged liquidation:
- First threshold: Warning and time to add collateral
- Second threshold: Partial liquidation (25%)
- Third threshold: Larger liquidation (50%)
- Final threshold: Complete liquidation
This gives users time to respond and reduces the system shock from mass simultaneous liquidations.
4. Real-time AuditingMonitor for oracle manipulation attempts:
- Cross-exchange price deviations
- Unusual volume on low-liquidity pairs
- Rapid position size increases before oracle updates
- Pattern matching against known attack signatures
The October 2025 attack likely showed warning signs. Someone dumping $60M of USDe at 5:43 AM should trigger alerts. If your monitoring didn’t catch it, your monitoring isn’t sufficient.
Conclusions: The $19 Billion Reminder
The October 10-11 liquidation cascade wasn’t caused by overleveraging or market panic—it was oracle design failure at scale. A $60 million market action was amplified into $19 billion of destruction because price feed systems couldn’t distinguish between manipulation and legitimate price discovery.
But this isn’t a new failure mode. It’s the same failure mode that destroyed bZx in February 2020, Harvest in October 2020, Compound in November 2020, and Mango in October 2022.
The industry has been taught this lesson five times, at increasing cost:
- 2020: Individual protocols learned, implemented fixes
- 2022: Regulators learned, began enforcement
- 2025: The entire market learned, paid $19.3 billion in tuition
The only question now is whether we finally remember the lesson.
Every platform handling leveraged positions must now ask:
- Is our oracle robust against known attack vectors from 2020-2022?
- Can our infrastructure handle cascade scenarios we’ve already witnessed?
- Have we properly balanced sensitivity with stability?
- Are we repeating the same mistakes that cost the industry hundreds of millions?
Because as five years of history proves, oracle manipulation isn’t a hypothetical risk or an edge case—it’s a documented, repeated, profitable attack strategy that scales with market size.
October 2025 demonstrated what happens when those lessons go unlearned at institutional scale. The attack wasn’t sophisticated or novel. It was just the same playbook, run against a bigger system, during a known vulnerability window.
The oracle is the foundation. When it cracks, everything above it crumbles. We’ve known this since February 2020. We’ve paid billions to learn it repeatedly. The only question is whether October 2025 was expensive enough to make us finally act on what we already know.
In modern interconnected markets, oracle design isn’t just about data feeds—it’s about systemic stability. Get it wrong, and $60 million can destroy $19 billion.
Get it wrong repeatedly, and you’re not learning from history. You’re just getting more expensive at repeating it.
Analysis based on public market data, platform statements, and five years of oracle manipulation case studies. Read Disclaimer for details.

![[Action required] Your RSS.app Trial has Expired.](https://8v.com/info/wp-content/uploads/2026/01/rss-app-cfAqZL-75x75.png)